In this article I explain how to configure basic security on FortiGate Firewall. Your network is divided into 3 roles which are WAN, LAN and DMZ.
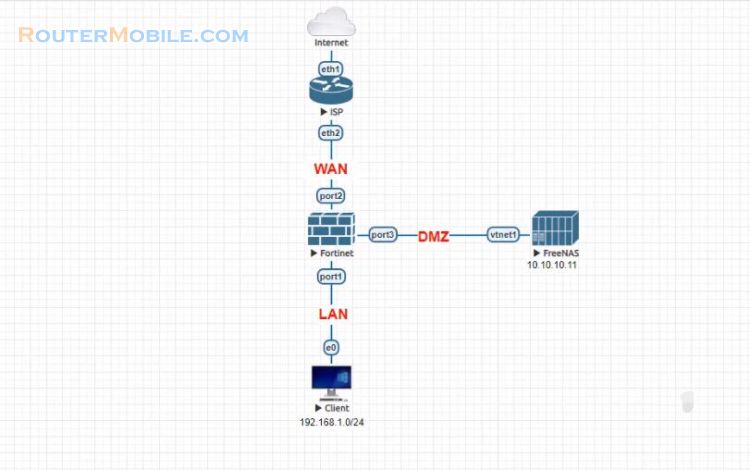
We have an example with a network with a file server. In this recipe, you will protect a File server by connecting it to your FortiGate DMZ network. In addition to protecting the File server, the DMZ also protects the rest of the network.
Go to network interfaces and edit the DMZ interface
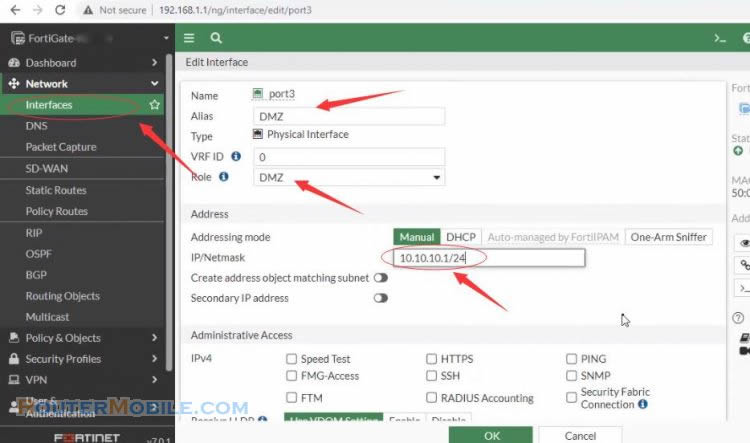
This example uses the port3 interface as the DMZ interface, port 1 as LAN interface, port 2 as WAN interface.
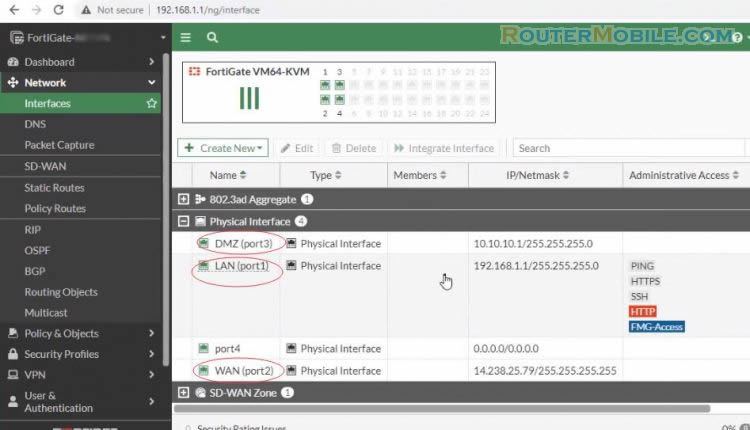
The interface Alias indicates that this is the DMZ interface. As well the Role is set to DMZ. For enhanced security, disable all Administrative Access options
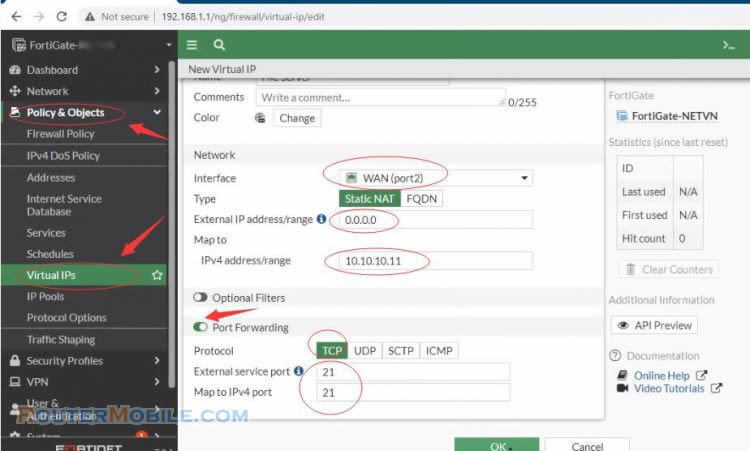
Go to Policy & Objects > Virtual IPs
Create a virtual IPs for FTP access. Mapping from the Internet to the DMZ interface.
Set the interface to the "WAN" interface.
External IP set to "0.0.0.0".
Mapped IP address, set to the internal IP address of the server you are forwarding to.
Enable "Port forwarding", Select "TCP".
Type in the port you want to forward.
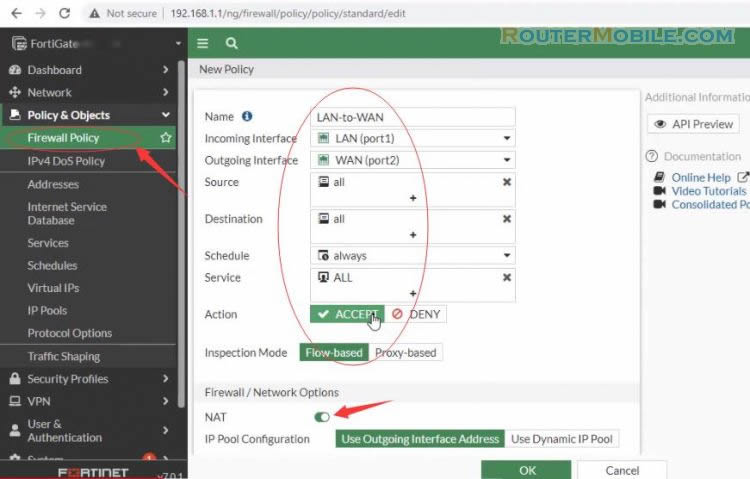
Go to Policy & Objects > Firewall Policy
Create a firewall policy to allow traffic from the LAN to the internet.
Give the policy and name that indicates that the policy will be for traffic to the internet.
Set the Incoming Interface to the lan interface and the Outgoing Interface to the Internet-facing interface.
Set Source, Destination Address, Schedule, and Services is all.
Make sure the Action is set to ACCEPT.
Turn on NAT.
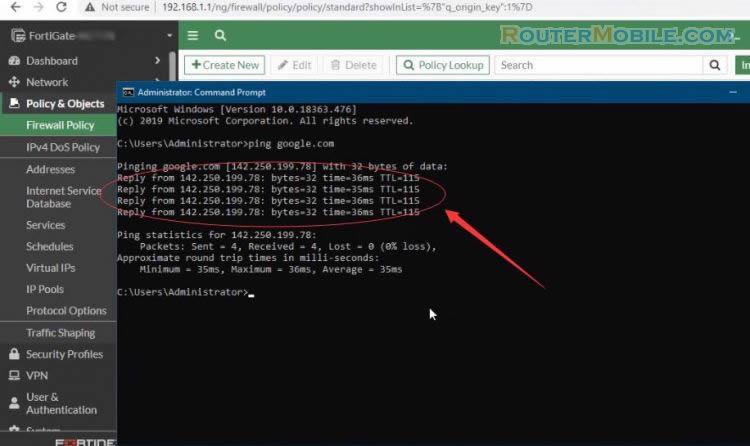
You can now browse the Internet using any computer that connects to the FortiGate's internal interface.
Create a second firewall policy to allow FTP traffic from the internal network to the File server.
Set the Incoming Interface to the lan interface and the Outgoing Interface to the DMZ interface.
Set Source, Destination Address, and Schedule is all.
Set Services is FTP.
Make sure the Action is set to ACCEPT.
Turn on NAT.
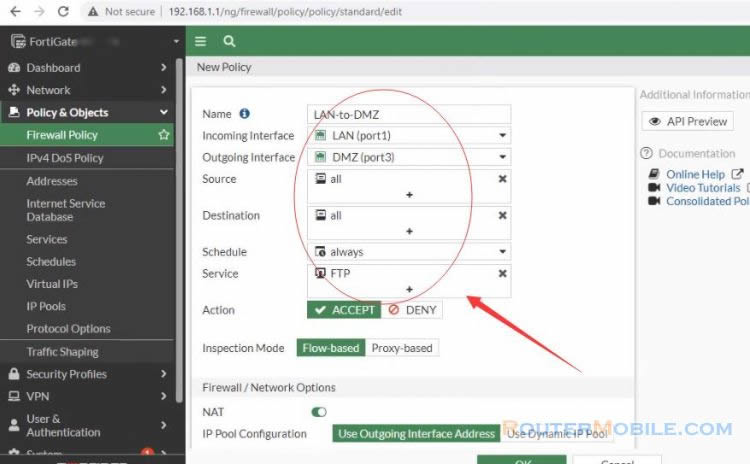
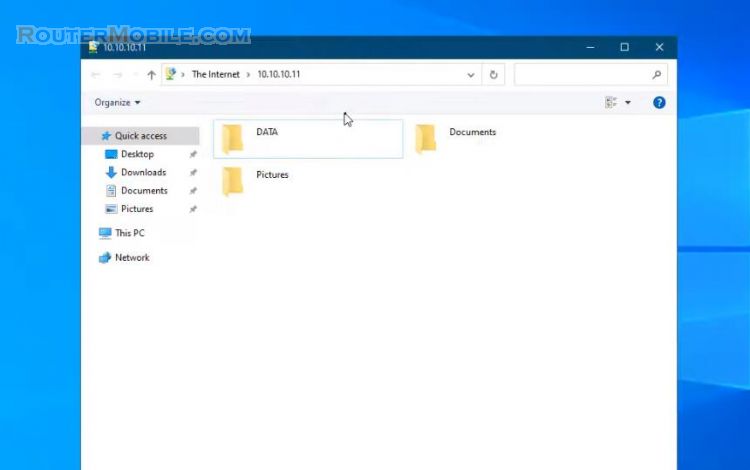
You can now access the file server from LAN address.
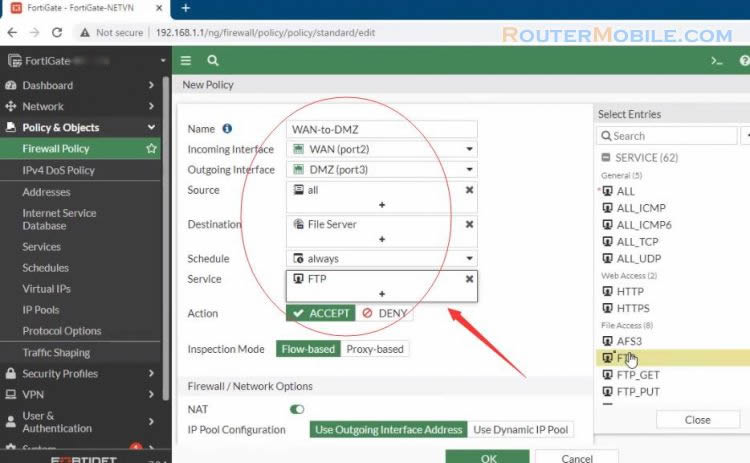
Create a third firewall policy to allow FTP traffic from the Internet to the File server.
Set the Incoming Interface to the WAN interface and the Outgoing Interface to the DMZ interface.
Set source and schedule is all.
Add virtual IP as the destination address.
Set Services is FTP.
Make sure the action is set to accept.
Turn on NAT.
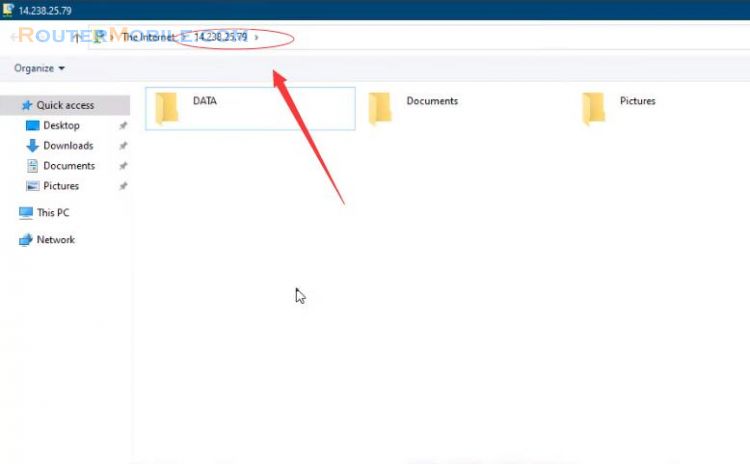
Internet users and internal network users can access the File server by the File server's Internet address. Internal users can also access the File server using its DMZ address.
In this recipe, you will protect a server by connecting it to your FortiGate's DMZ network. In addition to protecting the server, the DMZ also protects the rest of the network. A hole in the network protection must be made to allow outside users to access the server. This hole creates a potential vulnerability that is mitigated by the DMZ.
Facebook: https://www.facebook.com/routerbest
Twitter: https://twitter.com/routerbestcom